Endpoint Detection and Response Demystified
Endpoint Detection and Response Demystified
For years, Antivirus (AV) solutions were the major players on protecting customer endpoints. But as the threat landscape has shifted, we’ve seen the emergence...
...of newer solutions built to deal with some of the problems inherent in AV.
You may have heard the term “endpoint detection and response (EDR)” crop up over the past few years. These solutions were put on the market specifically to adapt to the evolution of the threat landscape. Replacing your AV product with EDR is definitively a step in the right direction, but choosing the right product is not an easy task. You are for sure wondering about how effective these solutions are in addressing the real-world threats.
I am sure most of you are already familiar with EDR products, what they stand for and what they offer. Anton Chauvin from Gartner® originated the term “endpoint detection and response,” using it to describe a, “family of new tools focused on visibility, and all from prevention to detection for the endpoint.” EDR solution can be best described as a comprehensive tool that expands AV into a whole new realm. Everything modern AV can do, EDR takes a step further—providing greater security and (more importantly) peace of mind. These functions include, but are not limited to:
-
Monitoring
-
Threat detection
-
Allow listing & deny/exclude listing
-
Threat Response
-
Integration with other cybersecurity solutions
EDR centers on protecting endpoints. Given the number of threats that emerge on daily basis, AV and other traditional endpoint security products can struggle with managing attacks across large numbers of endpoints. When we talk about traditional AV, it’s typically from a passive standpoint. AV can only detect and quarantine known threats, those that have been previously identified. Many AV solutions operate on traditional virus signatures. When a file gets discovered as malware, it generates a hash that then gets added to a virus signature database. This is called a reactive protection. What this means is that threat needs to be discovered first in order to create signatures that can enable detection and protection from this specific threat. This also means that someone had to get hit with a specific malware for this to happen. Which is all fine i guess, as long as you are not the one who got hit. Some AV products also use sandbox or they try to scan the code as additional security layer or a 0-day protection. But there are different types of advanced malware that can easily evade this type of protection:
-
Polymorphic malware
-
Weponised documents
-
Browser drive-by downloads
-
Fileless attacks
-
Obfuscated Malware
EDR, on the other hand, uses proactive protection. Some EDR products use definitions as well, but they do not rely on it. EDR solutions use integrated machine learning and advanced artificial intelligence (AI) to identify in real time weather a process is malicious or not and address it regardless of whether there’s a signature. Instead. That means that EDR products do not need an active internet connection or constant updates to provide protection. EDR solution uses a set of pre-execution and post-execution engines to look for threats and unusual behaviors on an endpoint (compared to a baseline), then takes action accordingly.
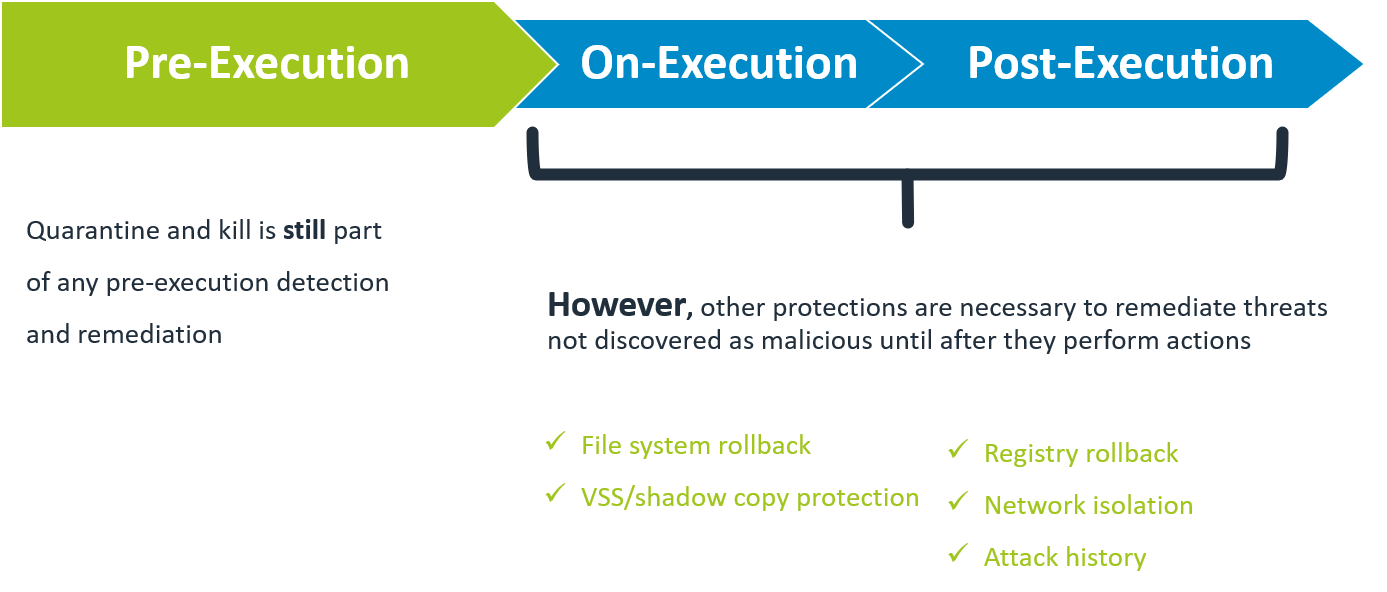
Quarantine and kill is still a part of any pre-execution detection and remediation, of course, regardless of the product, but other protection layers are important as well. We have seen that privilege escalation and lateral movement are among most common techniques used in attacks and to be able to detect and prevent this type of activities is half of the job. EDR solutions go a step further and offer file system and registry rollback functionalities, network isolation and complete attack history which is crucial for forensic purposes. This basically means that an EDR product, when configured properly can on a detection of malware or malicious activity isolate the end point on network, use the shadow copy to roll back any changes done to the endpoint (encrypted files, added or changed registry entries) and give you the full report/history of the incident.
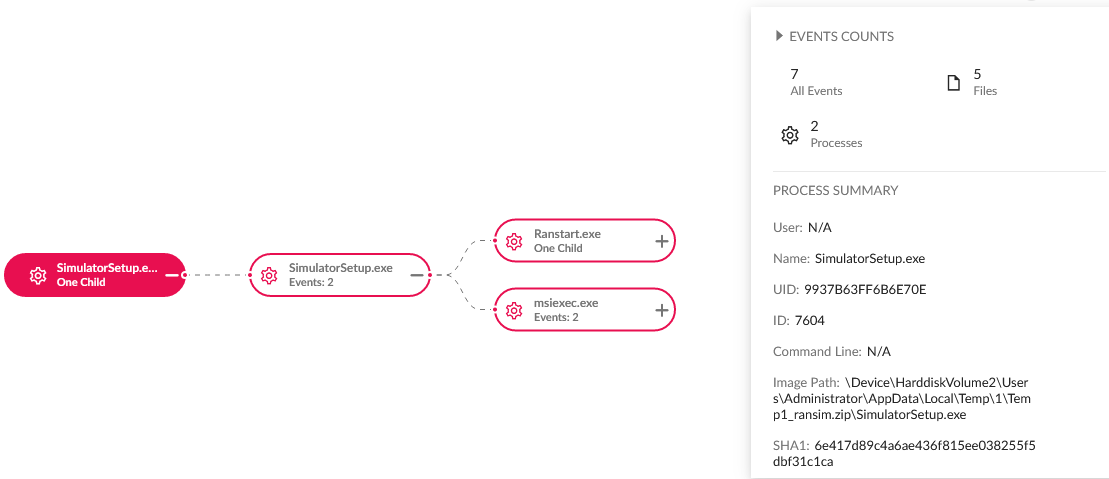
But malware and viruses are not the only thing we need to worry about. There is a big number of threat actors out there, groups like Conti, BlackMatter, Darkside, Revil etc. that offer Ransomware as a service and other different types of malicious services. These malicious actors use a wide set of tools and techniques to compromise environment, exfiltrate the data and delete their presence. Having an AV product as a protection against this is simply not enough. But, how do you decide which EDR product is the right one? Luckily for us MITTRE ATT&CK Evaluations can give us a better insight into EDR solutions and how they perform against real world scenarios.

One of the Evaluation that is really useful here is Carbank+FIN7 Evaluation which tested a large number of EDR solutions against two different attack scenarios (results of MITRE ATT&CK Evaluations can be seen HERE). From all EDR vendors included in this evaluation only SentinelOne EDR had 100% detection rate with 0 missed threats providing highest possible detection and protection rate on the market. In nestec portfolio SentinelOne comes as a part of N-able product group. In case you want to know more about SentinelOne you can find additional info HERE.
Threat landscape is constantly evolving and we see new type of malware, infiltration tactics and techniques and vulnerabilities emerge on a daily basis. If you want to protect your environment from most advanced threats you need a product that is always one step ahead of threat actors. There is no such thing as total protection, but having a proper EDR product in your environment brings you pretty close to that. There is no point in waiting for incidents to happen, open your free trial and make sure that you are properly protected:

