N-able MDR vs EDR - Explaining the differences and advantages of MDR
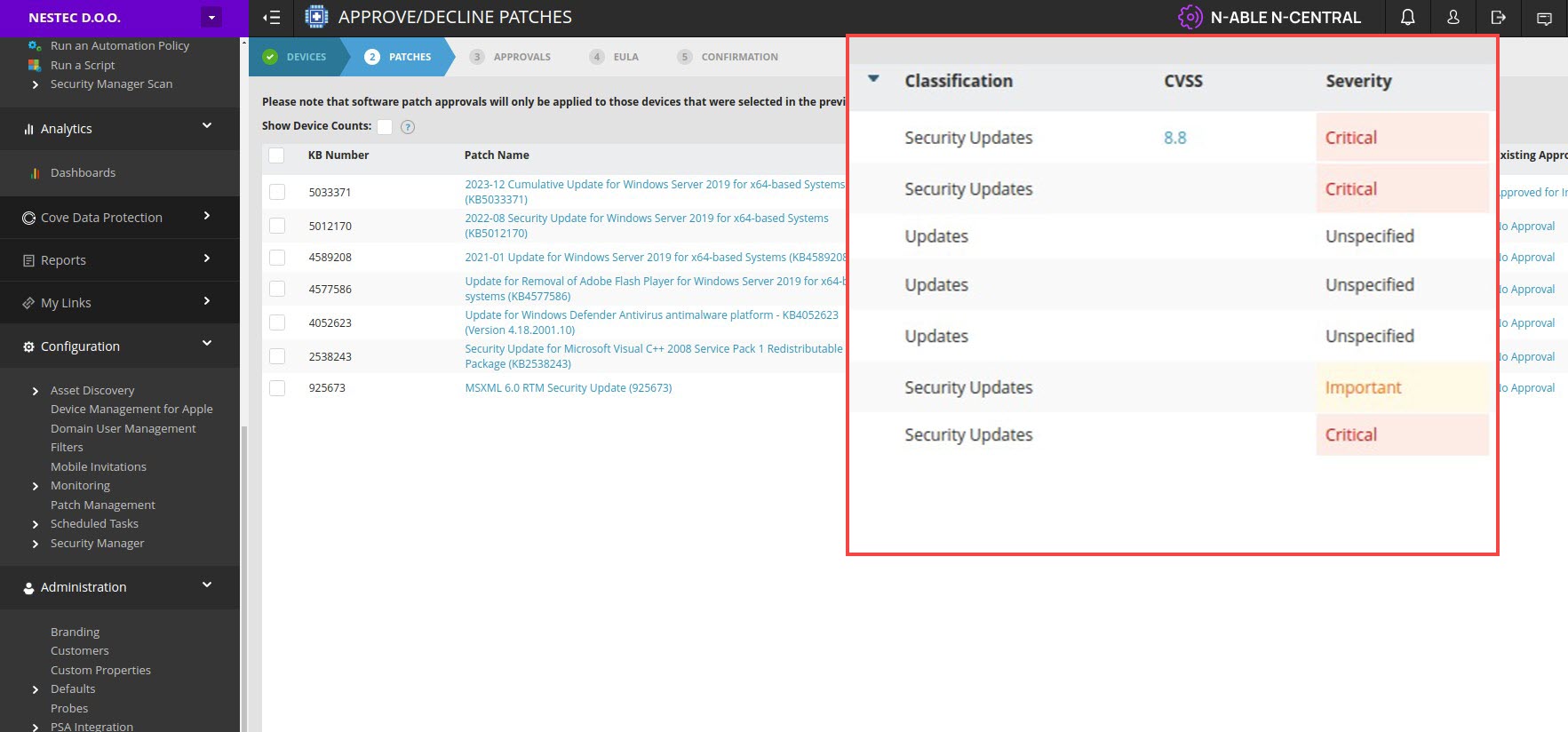
With N‑able Managed Detection and Response, experienced cybersecurity analysts enhance your current team’s capabilities and help you reduce threat detection and response times while giving you complete visibility.